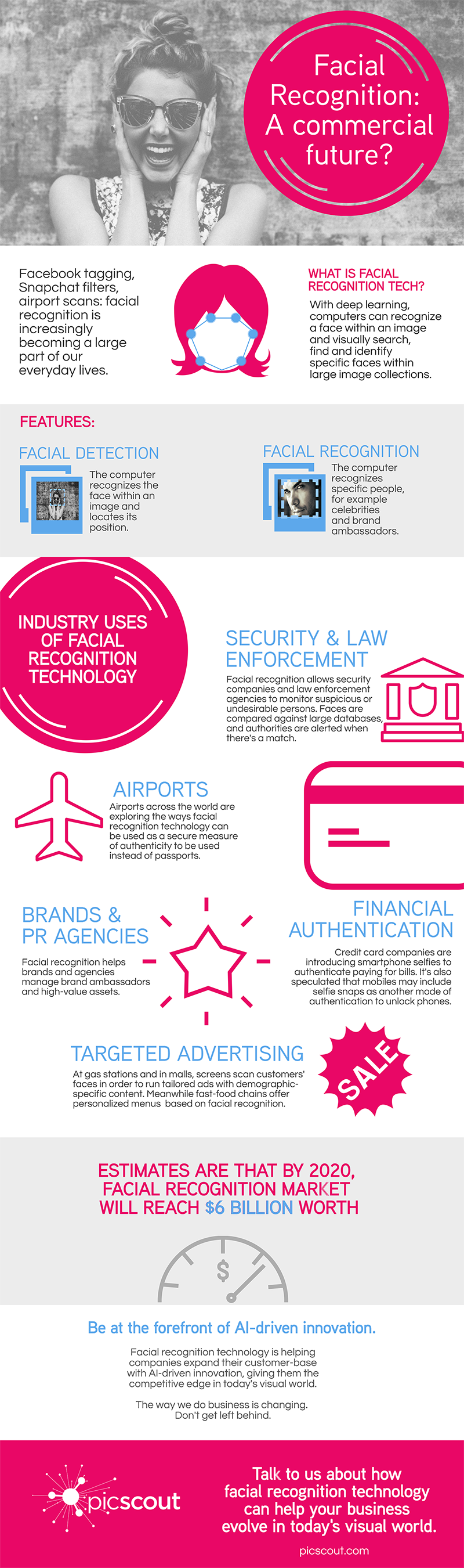
What if the Oscars were determined by the amount of images online of each nominee? Analyzing an actor’s visibility is a precursor to media monitoring their presence — and for this year’s Oscars awards, we did exactly that.
This year’s Oscars is a tight race, with outstanding performances being outplayed by heavy promotion efforts. Trending actors predicted to win have a visual buzz — the number of images often correlates with their fandom, media support, and various marketing strategies by the film’s producers, their agency, and others.
So we asked ourselves, does visual presence affect the eventual winners of the 88th Academy Awards? How would it affect the voters’ perception of each actor, each category? Are the awards based on merit, politics, or marketing? As the voting by members of the Academy of Motion Picture Arts and Sciences closed on Tuesday, we applied some image-based media monitoring and tallied the results for the Most Visual Performer Award.
Best Supporting Actor:
It’s a tight race between Mahershala Ali (Moonlight) and Dev Patel (Lion): both would make Oscar history if they take home an Academy Award next week. Patel would become the first actor of Indian descent to win an acting Oscar or Ali would be the first Muslim to win an acting Oscar.
Ali was considered the favorite after winning a Screen Actors Guild award for his role in Moonlight, but now Anglo-Indian Patel has joined the front of the race following his BAFTA victory for Lion.
Winner of PicScout’s Most Visual Performer Award (Supporting Actor): Mahershala Ali
Best Supporting Actress:
It’s widely assumed that the versatile Viola Davis will take home the Oscar this year, since scooping up nearly every other award in the season for her moving performance in Fences. By media monitoring her presence, her visual buzz leading up to the Academy Awards is close to 40% — nearly double that of the runner-up, Nicole Kidman.
Winner of PicScout’s Most Visual Performer Award (Supporting Actress): Viola Davis, no competition.
Best Actor:
Visually, it’s a battle of the heartthrobs — Ryan Gosling (La La Land) and Andrew Garfield (Hacksaw Ridge) are in close sights for the Most Visual Performer Award. While neither of them are considered to be serious contenders for the Academy Awards, both of them are closely linked to the visual favorite of the awards season — Emma Stone. Gosling was her La La Land co-star and Garfield has been her on-again, off-again partner for over 7 years. With today’s clickbait celebrity obsession, their visual presence while media monitoring isn’t so surprising.
What is surprising is how they compare to the low image results of the two actual contenders for the award — Denzel Washington (Fences) and Casey Affleck (Manchester By The Sea).
Winner of PicScout’s Most Visual Performer Award (Best Actor): Ryan Gosling, thanks to Emma Stone and swooning fans.
Best Actress:
Emma Stone. Emma Stone. Emma Stone. La La Land’s lead actress dominates the visual buzz surrounding the 89th Academy Awards: she takes up 50% of the images found in her category of Best Actress (runner-up Natalie Portman was next in line with 21%). In more comprehensive media monitoring, Stone also featured in a fifth of all images found of every nominee across lead/supporting actor/actress categories in 2017. Our money, as well as those from the La La Land team, is on her.
Winner of PicScout’s Most Visual Performer Award (Best Actress): Emma Stone.
Best Film:
La La Land has been the Oscars front-runner since its release — it tugs on the heartstrings and nostalgia of Academy voters with music, color and Hollywood dreams. Its visual dominance across the web and social media peaked at the start of the awards season and as “front-runner backlash” kicked in, its visual presence decreased as it neared tonight’s Oscars ceremony. Still, La La Land will take both the Academy Award and PicScout’s Most Visual Performing Film award — its the kind of movie that awards bodies absolutely love.
Winner of PicScout’s Most Visual Performing Film: La La Land — could it be anything else?
FUN FACT
There are thousands more images of our Best Actresses and Best Supporting Actresses than their male counterparts.
Images courtesy:
Viola Davis, Emma Stone, Andrew Garfield © Gage Skidmore
Mahershala Ali, Dev Patel © Gordon Correll
Nicole Kidman © Eva Rinaldi
Ryan Gosling © Georges Biard
Natalie Portman © Josh Jensen